SS week5
Symmetric Cryptography(Con’t)
Stream Ciphers
A5/1 Cipher (GSM)
- Produces keystream bit at each step
- Easy to implement in hardware
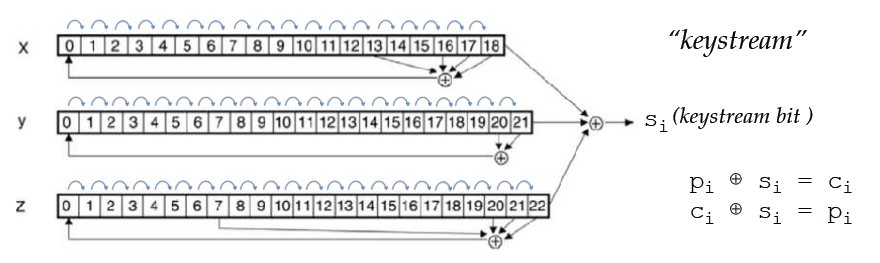
RC4 Cipher
- Produces keystream byte at each step
- One of the most widely used software stream ciphers
- in older implementations of SSL /TLS; WEP(!)
- removed from major browsers in 2015
Block Ciphers
- Feistel Cipher
- key will change every round
- function F must be reversible
- multiple “rounds”

Block Cipher Modes
- Electronic Code Book (ECB) Mode

- 將plain text切成 blocks
- 分別對每個block做Block Ciphers
- 缺點:同樣的block會被加密成同樣的cipher
- diffusion較差
- Cipher Block Chaining (CBC) Mode
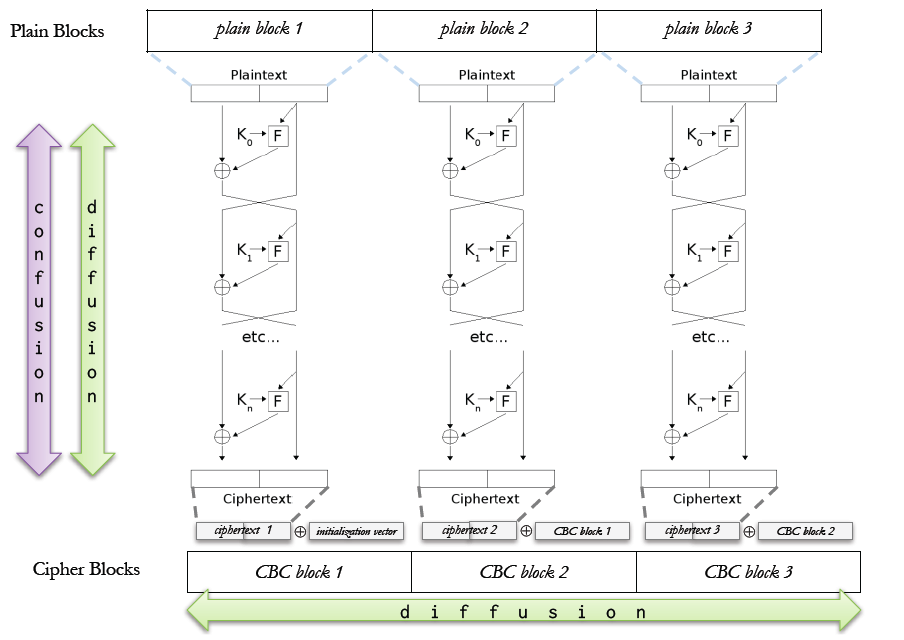
- 跟ECB類似
- 在做完Block Ciphers,會在跟前一個block的結果做xor,成為最後加密的結果
- 改善diffusion
- 最後一個block可以當MAC blocks(包含整個plain text的資訊)
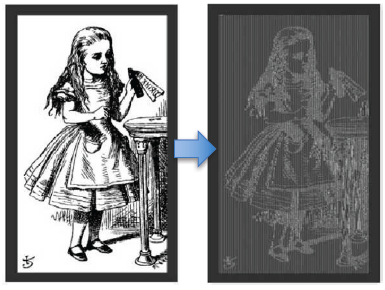
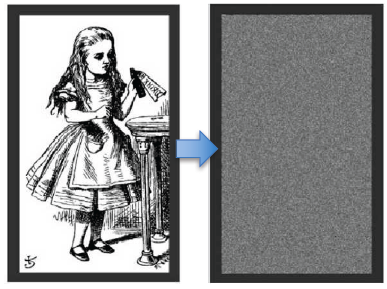
Comparison
ECB V.S CBC
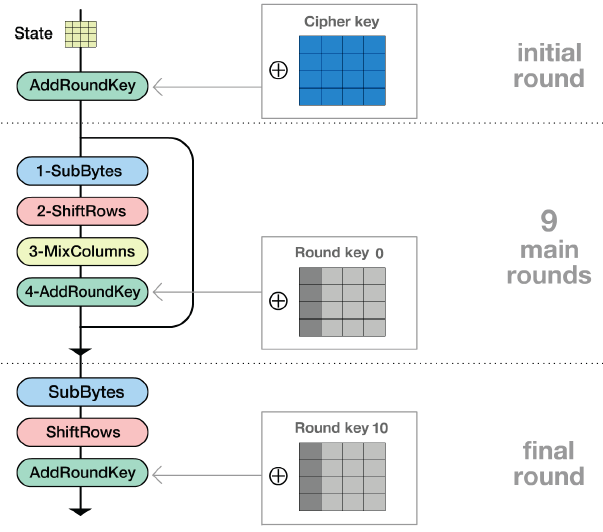
AES Cipher
- most popular nowadays
Symmetric Key Ciphers and Key Reuse
Depth Attacks : Giving attackers deeper information about your plaintext or key
- 例如之前的one-time pad ,當key重複使用時,攻擊者可以得知P1 ⊕ P2

Replay Attacks:
- 當攻擊者監聽到一個Ciphers,傳送給對應的人,一樣可以得到正確的回覆

Using a Nonce(one-time use random bytes)
Countering Depth Attacks :
當key重複使用時,還是可以因為nonce不同,而加密成不同的cipherCountering Replay Attacks :
當攻擊者監聽到一個Ciphers,想要重送時,會因為Nonce不同,而被拒絕。
Hashing
- No key from the user (built-in key)
- One-way function only (cannot reverse/decrypt)
- Compresses data to fixed length (e.g., 128-bits)
- Collisions exist, but should be extremely rare
Non-cryptographic Hashing
Cyclic Redundancy Check (CRC)
- 👍 Data Lookup
- 👎 Data integrity
pro
- simple to perform in hardware
- can catch common, unintentional errors
cons
- cannot catch intentional manipulation
- easy to revers
- crc(x⊕y⊕z) = crc(x) ⊕ crc(y) ⊕ crc(z)
well-known design flaws of the Wired Equivalent Privacy (WEP) protocol
Cryptographic Hashing
- Sha1 sha2
- md5
- …
Data Integrity: MAC blocks(Message Authentication Code)
- protects both a message’s data integrity as well as its authenticity, by allowing verifiers to detect any changes to the message content.
- 在解密前先驗證資料來源及正確性(有沒有被變更)
- 沒有先驗證就解密的話,攻擊者能從更改後的cipher跟plaintext中得到額外的訊息
Approaches to Authenticated Encryption
- MAC-and-Encrypt
- encrypy the plaintextthen calculate MAC on plaintext
- MAC-then-Encrypt (MtE)
- calculate MAC on plaintext and encrypt plaintext + MAC
- vulnerable to Decryption Oracle Attack
- ∵ you have to perform decryption before Authenticated
- Encrypt-then-MAC
- encrypy the plaintext then calculate MAC on cipher
Coding time ~
So many things to care about
- which algorithm to apply(must be not broken yet)
- implements a algorithm wihout making mistake
- generate different keys
- use nonce
- Authenticated Encryption order

##Developers should know about cryptography!
##But only cryptographers should write ciphers!
NaCl
- NaCl : a new easy-to-use highspeed software library for network communication, encryption, decryption, signatures, etc.
Implemented in C
- libSodium : portable, cross-compilable, installable, packageable fork of NaCl
Implemented in C
- RbNaCl : Ruby binding to the Networking and Cryptography (NaCl) library
Implemented in Ruby, but you have to install libSodium yourself
- rbnacl-libsodium : packages the libsodium library as a Ruby Gem
Implemented in Ruby, the only thing to do isgem install rbnacl-libsodium
灑花( ̄▽ ̄)/‧☆“‘ *-.,,.-*‘`”*-.,☆